We’ve been telling enough about the advantages of alternative data and risks associated with collecting conventional data on your borrowers. Today we will demonstrate how personal data usage can not only turn into risk and damage for the financial institution’s working process but also spell disaster for the whole business. We will draw on several cases from our experience, which are: Seasonal Aggravations, Fraudulent Brute Force Attacks, and the Black Swan. What are these risks and how to get protected?
Seasonal attacks
New Year’s Eve is a magical time when all our wishes come true. But to really make them true, a grown-up dreamer has to be a good employee for a whole year. If you want something more, you can always call on a lender, and your credit will be surely approved – after all it’s December, the most wonderful time of the year! We expect everyone to be a little kinder, and a credit to be given as easy as a present to be found under the Christmas tree.
To be serious, there is a strong consumers’ belief that big holiday period is the time when credit institutions are happy to approve a loan everyone who needs some spare money and asks for it. Spoiler alert: that is not true. Neither the seasons, nor the weekends or holidays have any effect on the approval range or the risk policy extent.
Yet the demand grows and the number of loan applications grows dramatically as well. As a result, during this “high season” you will receive 100 applications instead of the average 10, for example. Supposing that each tenth application would be fraudulent, we should say there will be ten times more of them than normally. For credit institutions, such a flow is extraordinary yet natural and casual. And as it is casual, it is possible that you will not focus enough on the growing risks.
Nevertheless, these seasonal attacks bring a lot of troubles due to the growing percentage of the “black sheep”: it’s been several years that we register an increase in the number of fraudulent applications at the end of December. The number of such fraudulent requests frequently grows by several times.
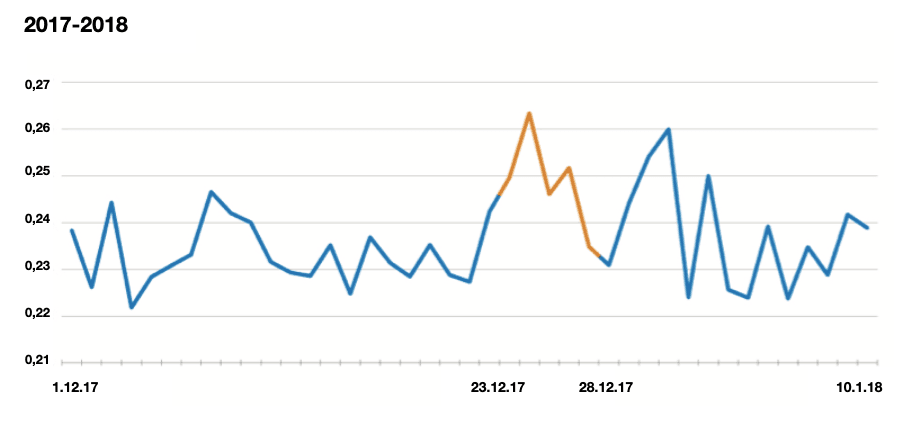
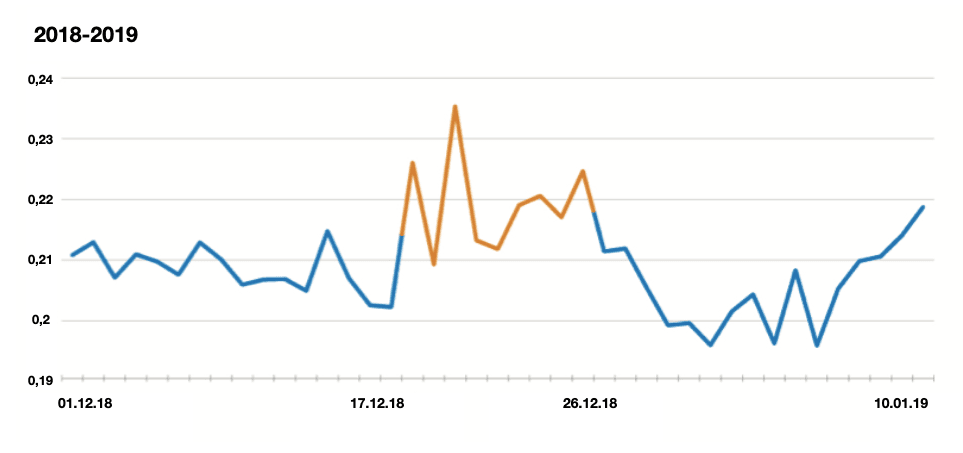
Incoming applications risk level at a credit institution in December 2017 and 2018. A significant growth of fraudulent applications of a high risk can be seen in the twentieth of December. At this moment, the institution is exposed to a higher share of fraudulent applications.
It can be seen on the graphs that the late December was loaded with credit applications on general and risky applications as well, both in 2017 and 2018. What should a credit institution do in this case?
In order to neutralize such seasonal attacks, we recommend taking a more prudent look on the risk policy. The “seasonal” fraud is usually not of a profound background and most of the risky applications can be easily cut off, saving the business from collateral damage.
Basically, the most efficient way to protect yourself against this type of fraud is setting more rigorous cut-off levels after existing patterns. Of course, this will lead to rejecting some reliable clients too, but if we have to choose between safety and greed, it’s better to choose the first one. The missed profits can be compensated by offering credits with extended limits to a well-known and reliable part of your portfolio.
Fraudulent brute force attacks
Let’s think of the DDoS attacks, familiar to anyone related to online lending. A cybercriminal overloads the incoming channel with an enormous number of applications in a short period of time until the system breaks down or the security tools kick in, cutting off the source of the threat on one or several IP addresses. In such a case we imagine one or several malicious computers which are the source of the attack and an army of zombie devices willing to destroy their aim.
When we talk about fraudulent brute force attacks, it becomes more complicated. Such an attack is launched from a big number of devices which are no “zombies” but have an individual IP and some supporting data preventing them from being cut off by conventional security tools in one operation.
They also aim at finding weak points in the applications screening system. Such weak points are requests to the data sources which make the basement for the whole system. Credit bureaus, telecommunications operators and other data suppliers give information valuable for the workflow and used in the credit decisioning.
Each supplier has its own limit on requests from a client (credit institution) to be processed. When the limit (usually the lowest) is overcome during an attack, the source is being backed up or falls out of the processing. A security leakage appears where the whole flow of risky applications swoops down to. The decision is taken at random then and the whole flow is being identified either as reliable which brings direct damage or as neutral and is being transferred to manual processing, which slows down the whole thing and draws in the number of credits approved, that is, some profits missed.
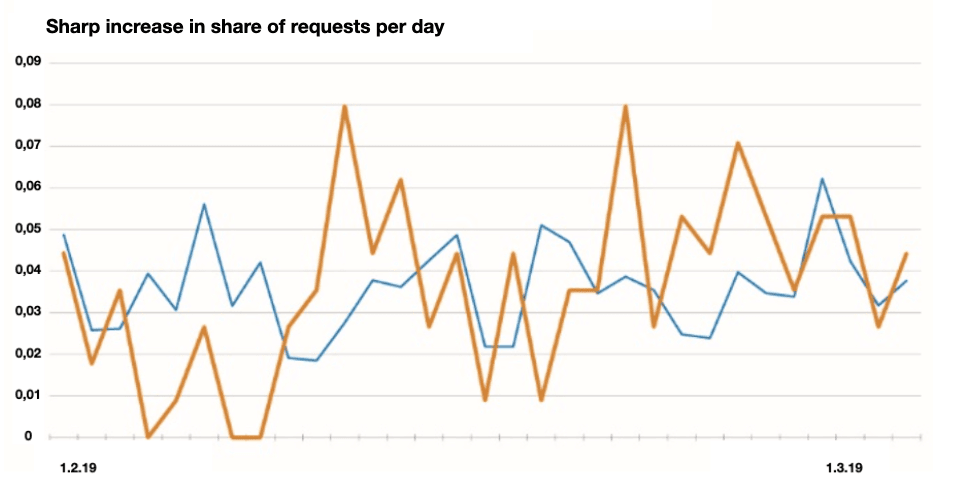
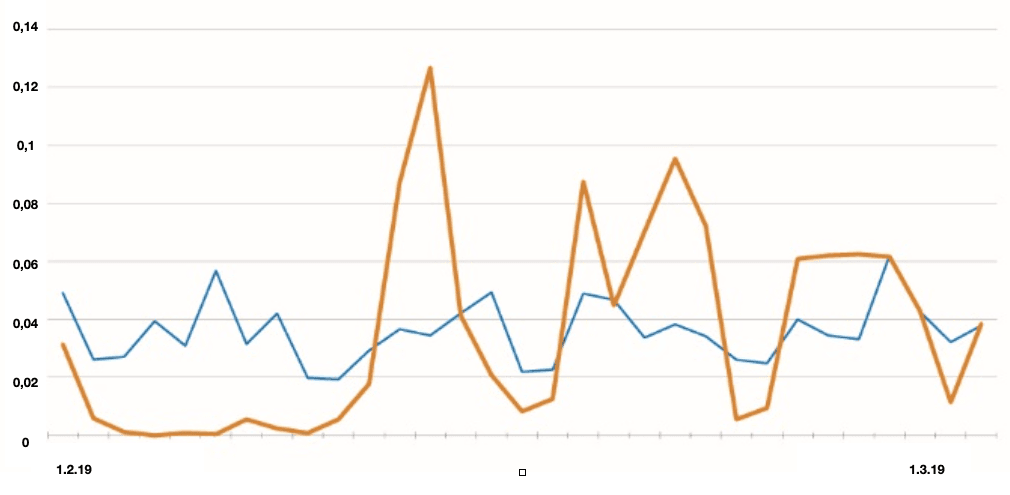
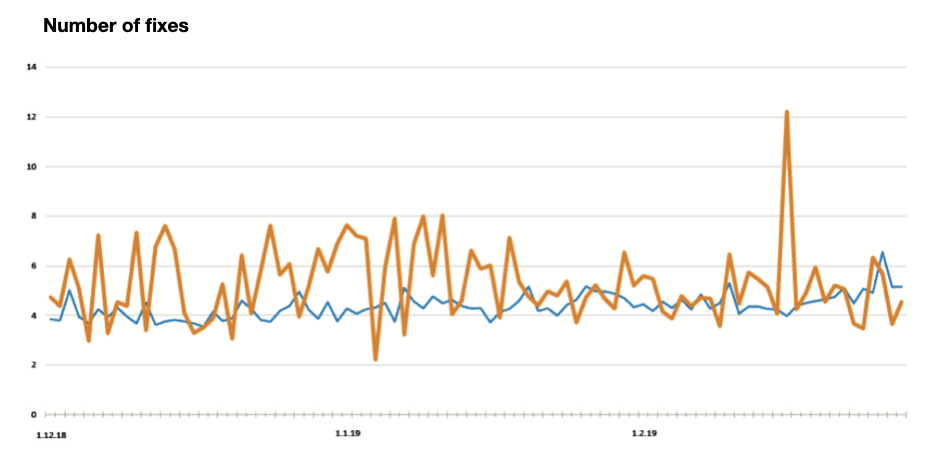
An average incoming flow of applications on clients (blue) and two financial institutions from Southeast Asia (orange), affected by a Fraudulent brute force attack in February 2019. The number of risky applications grew by 3-4 times, which looks abnormal compared to the average level and out of proportion to the normal incoming flow at the beginning of the month.
How could we deal with such evil? The most efficient solution would be monitoring the risk level using fraud score detecting and blocking the most suspicious and active devices, analyzing application frequency from the IP address and subnet. Yet such a method implicates a constant control over the incoming flow by risk managers.
The “Black Swan”
“Storing and using personal data is dangerous”, we keep telling this over and over again. Sticking to our today topic, we will demonstrate how dangerous it can be. Let’s think for a minute about the worst: another data leakage has occurred and it has end up in the black market. But this time it’s not only about ID details of a client, but all personal data, all the sensitive information, all we had about residence addresses, IDs, insurance numbers, tax reference numbers and any changes made to this data for several years. And it’s not about one unlucky client, but one hundred employees of an unfortunate company in a nameless town.
The situation is fictional of course, yet the threat is more than real. At fraudsters’ disposal, such a data set would be an absolute Black Swan, and the conventional data processing system has no solution against it.
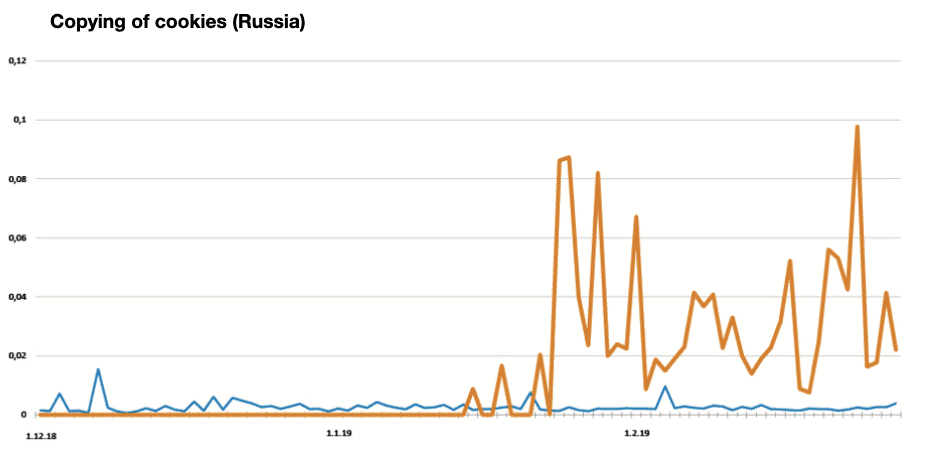
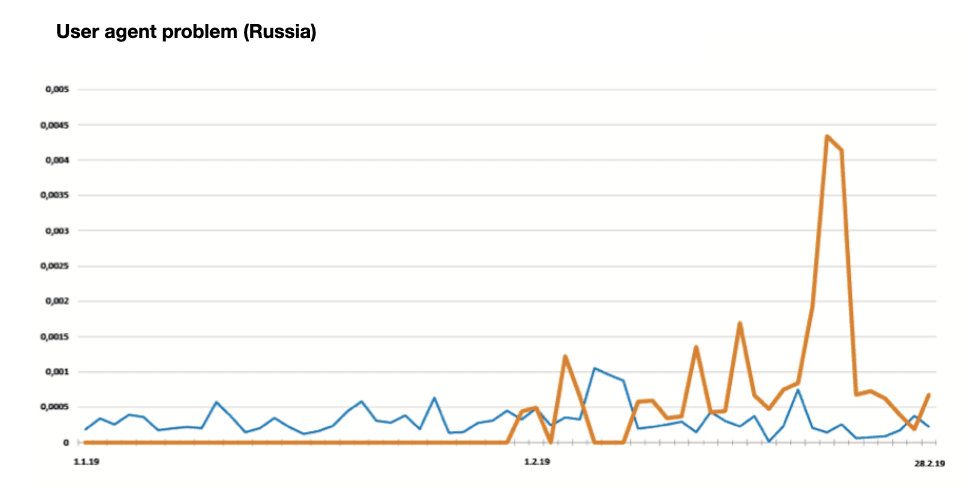
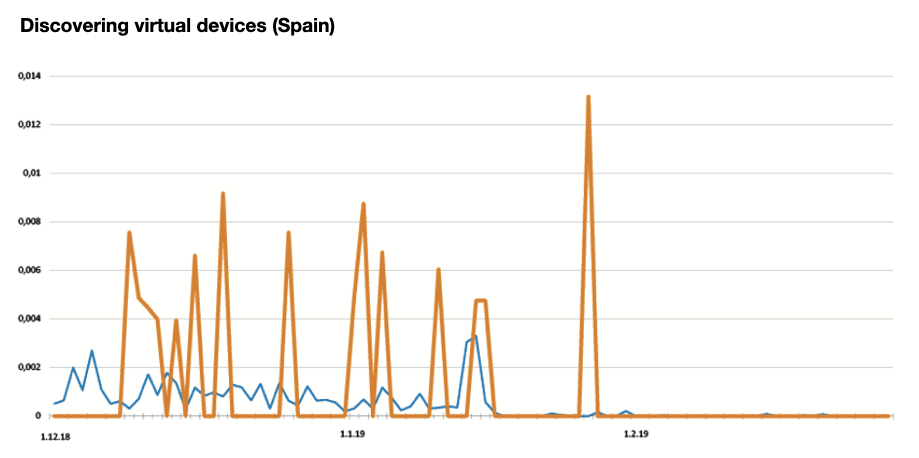
Several “black swan” cases. Average clients’ figures (blue) against clients exposed to the attack (orange). We can see an abnormal grow of risk rating by 4 times.
Although consequences of such attacks are severe, they are not commonplace. It is possible to get prepared, bringing in extra tools of data and loan applications analysis and using poorly reproducible alternative data in the loan workflow.
Thus, detecting repeated devices, combined with cross-checking the data used in different loan applications sent from a same device along with analysis of large deviation markers could be useful.
We hope that the cases demonstrated in our article will foster clients’ determination to use alternative data and extra tools for loans approving and security. It’s useful to remember though that fraudsters do not stay behind in their methods as well, which means that we should always be on our guard.
Our service is a relevant tool to fight against fraud, in line with the today’s realities. It will help you to reduce significantly the consequences from the attacks described above. Yet how useful this tool can be depends on the man, that is, the risk manager who is familiar with modern security tools, literate in data use and understands the incoming signals, has a fast track to handling the threats and helps the business to develop in a most successful way.
Take care of yourself!
Your Juicy Team