Along with the opportunities global digitalisation has brought us risks. The emerge of a large number of online businesses inevitably leads to a fraudulent traffic increase. Based on our experience in dozens of countries we can spot more than a thousand patterns of fraudulent behaviour, which, unfortunately, are constantly being improved by scammers. However we also believe that exploring the new methods of risk assessment gives much better result in terms of online fraud fighting than another superficial set of risk markers, which may be used as filters for automatic denial.
Today we are going to share our new methodology benefits, which allow online businesses to identify high-risk and carry out segmentation throughout the entire flow of applications. We are also proud to announce the launch of our new product: automatic risk management reporting, which will be available to all our clients in Q1 2023.
The aggregated results show a comparison of fintech companies in different regions of the world, data are given as of November of this year.
Our methodology is based on the division of the entire session space into 4 groups, which are the following:
The key positive factor of this approach is that all the high-risk sessions inevitably fall into one of the four groups, therefore, we can spot 100% of all possible online fraud attempts.
Another advantage is that this approach does not depend on the country, technologies, local legislation etc., which means that one can compare various online resources and countries.
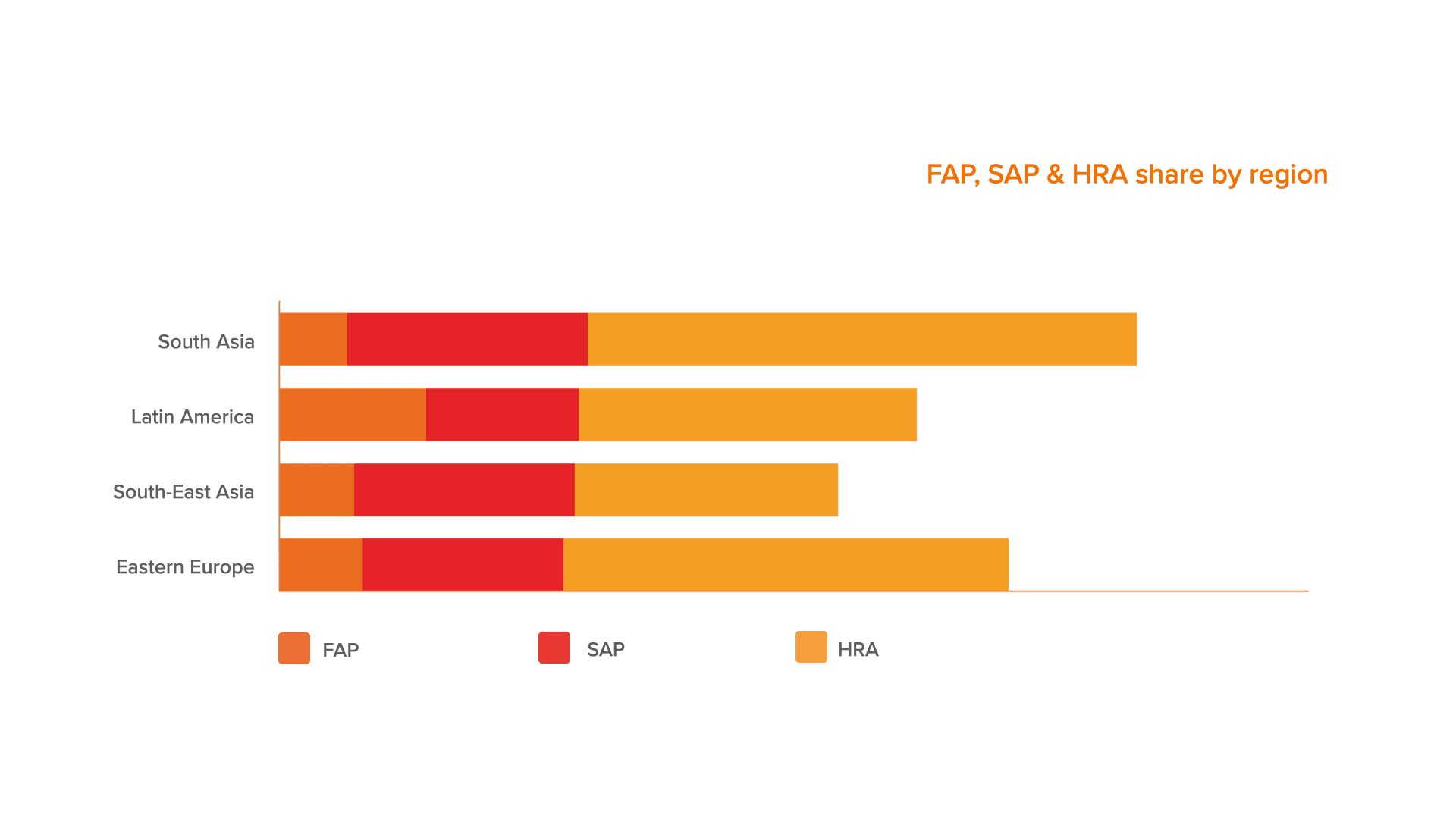
Here you can see the share of FAP, SAP & HRA, which sums up the level of toxic / high-risk sessions by region.
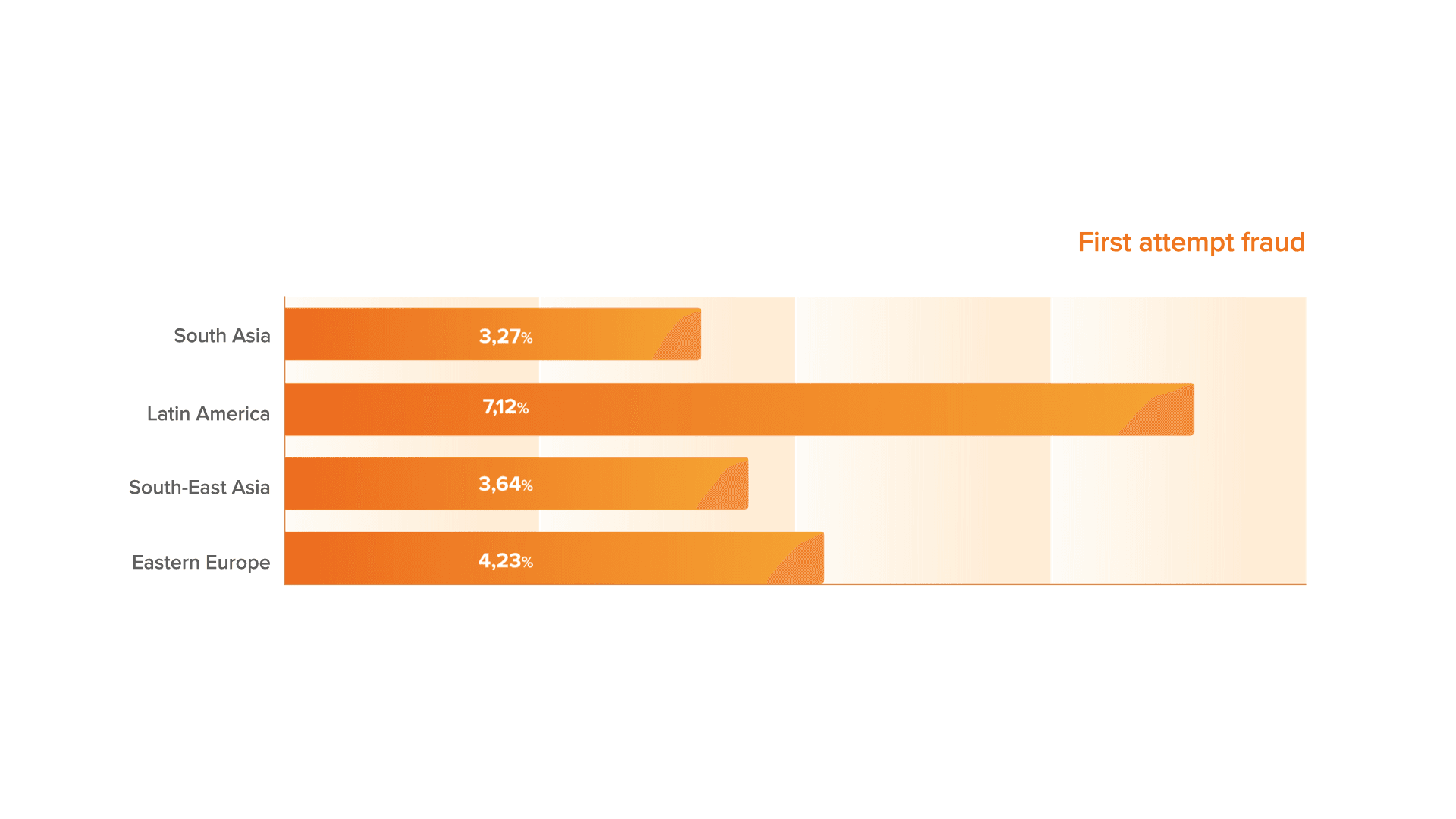
In the First attempt fraud category we included a combination of 50+ rare events with a high probability of fraud related to a device technical manipulation, in particular, the use of randomizers, some browser or operating system anomalies. We also noticed that the number of First attempt fraud in Latin America exceeded the same indicator in other regions almost two times, which may be an illustration of the increase of single fraudsters attacks in this region over the past month.
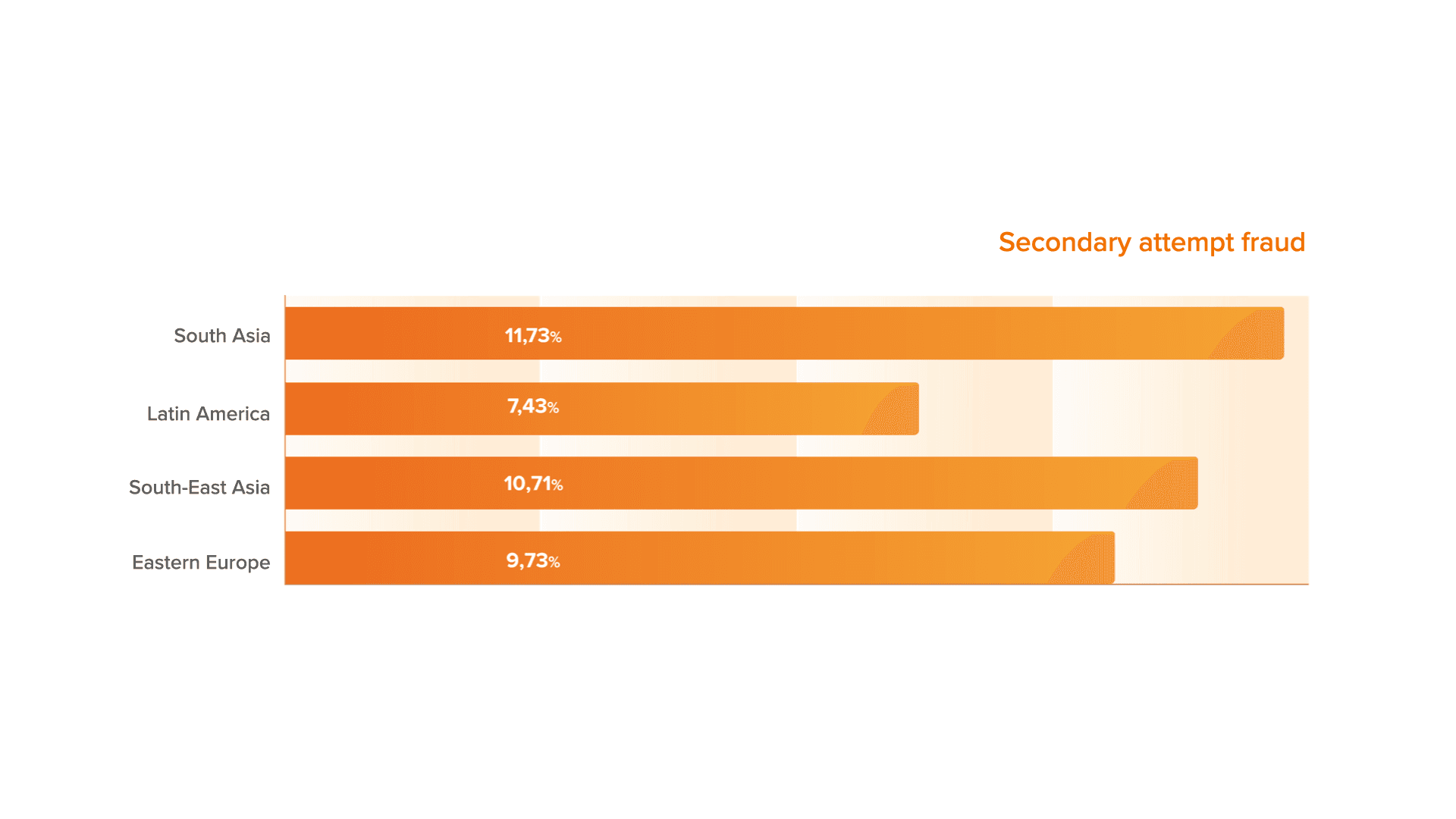
In Secondary attempt fraud metric we included repeated devices as well as repeated users. We also noticed that the number of Second attempt fraud in South and South-East Asia and in Eastern Europe remains at a relatively high level, which indicates that fraudsters have been using large amount of data from the fraud net recently.
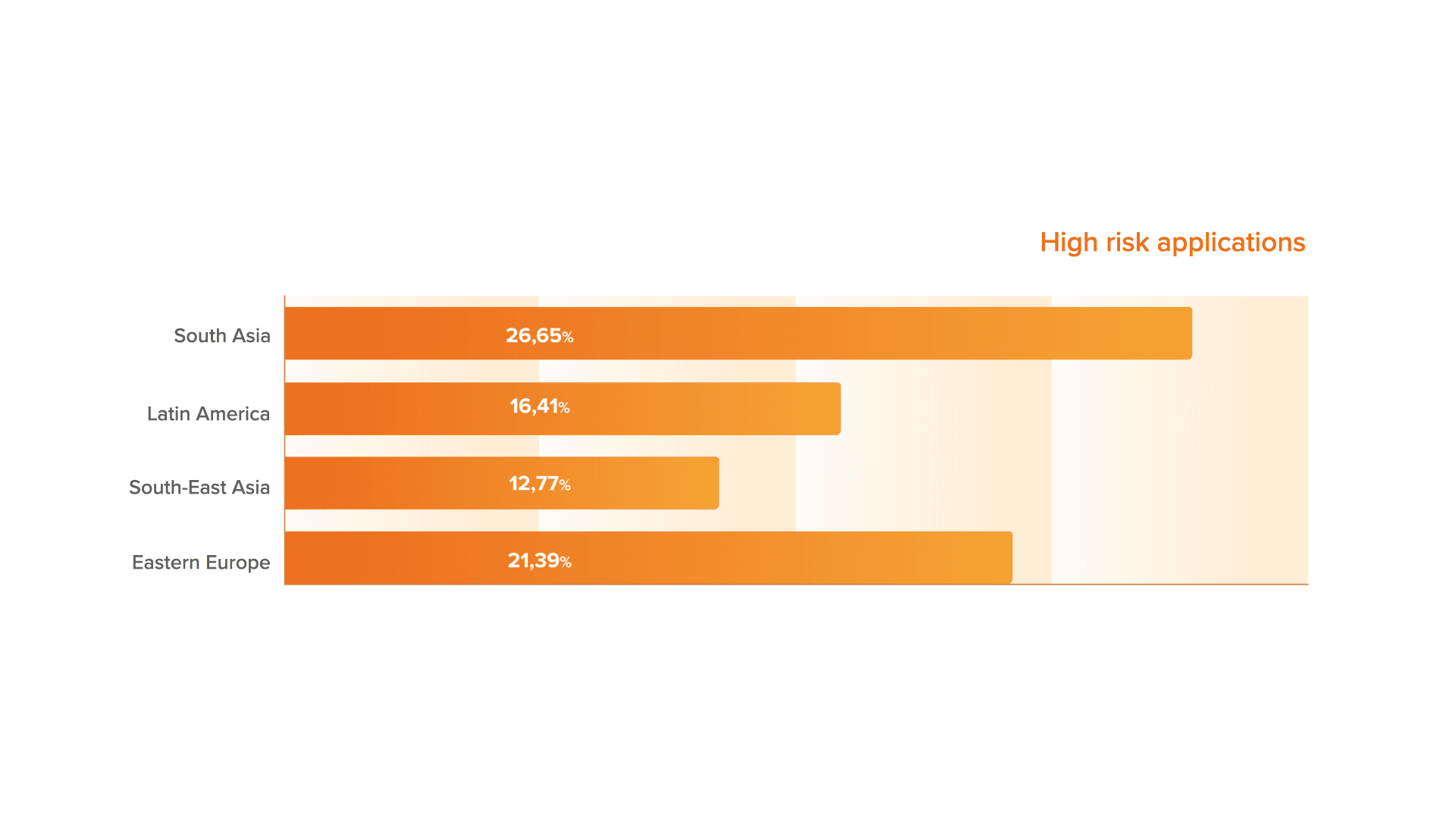
As you can see here, the level of high-risk applications in South Asia and Eastern Europe is the highest. Usually such figures occur in the countries with low income of the population and also may indicate the rise of a credit shopping in the region.
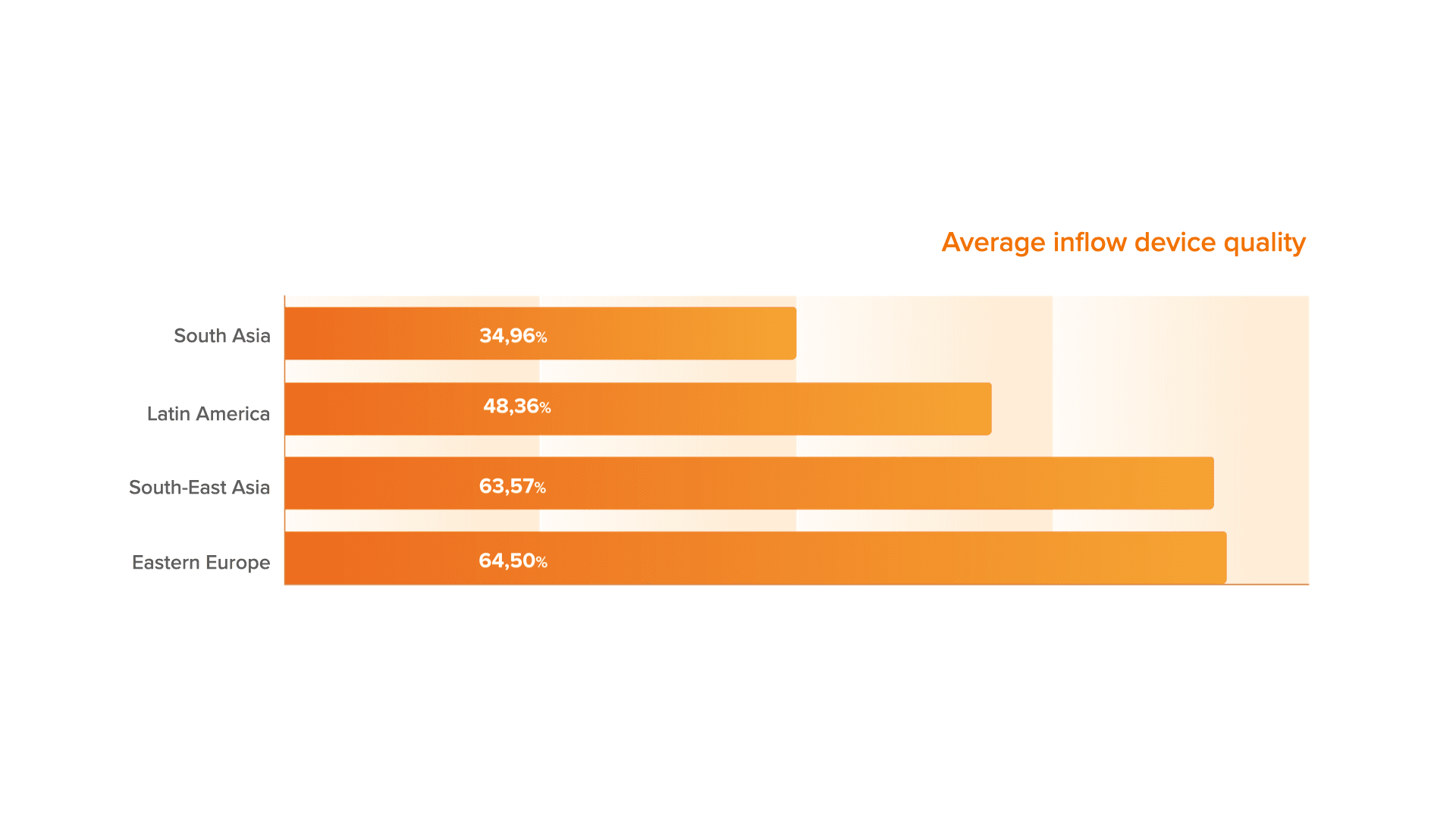
The highest level of average inflow device quality has been spotted in the regions of South-East Asia and Eastern Europe. The lowest rate has been recorded in the countries of South Asia.
In this regard, we recommend online companies to take into account the following actions:
- Fine-tune the process of regular reporting on key types of risk;
- Give credence to preparation of strategies and risk policies for dealing with different situations. For example, if your company has a high FAP compared to the average in the region, then you should look for a wide range of stop factors for identifying this type of risk; if you have a low flow value in terms of device quality compared to the region, then it will be useful to reconsider the current customer acquisition strategy;
- Make sure that the company has all the necessary technologies in order to detect the risk of fraud in real time - hundreds of fraudsters can attack the resource of a financial institution in a short period of time;
- Check if the data information value is sufficient to improve the quality of models and decision-making systems;
- Restrict the use of your users' personal data. Please note: often personal data is not required for auxiliary and vendor tasks - it is often possible to find an alternative solution based on anonymized sessions or tokens;
- Determine for yourself a work option in case of a partial failure of the online infrastructure and a conservative work plan in case of a massive fraud attack (reducing the approval level for applications, introducing additional methods of user verification etc.);
- Pay special attention to the user's behavior on your online resource in order to identify hidden correlations.
We are planning to create the system of consolidated reporting for all our clients in the nearest future.
