While anti-fraud tools keep strengthening, they become more and more effective. Oppositely, fraudsters are looking for new ways to skirt online fraud measures. Over the past few years, remote access technology has been on the rise among hackers, triggered by the rapid development of online digitalization.
This fact puts all online market participants at risk, especially when it comes to financial institutions, which risk significant financial assets. The latest stats confirm the underlying trend. A growing number of fraud cases feature remote access and social engineering technologies.
What are the main types of social engineering and remote access technologies
Current risks associated with social engineering and remote access technologies can be divided into three main groups judging by the type of impact on online consumers:
- Technical remote access - hacking into accounts and gaining access to a user's device with remote access technologies at the expense of various secondary technologies. Here is an example: fraudsters launch mass mailing that contains a link to download malware. Usually, they proceed on behalf of popular brands or banks. The email often contains a direct link to a site that looks real (or to a website with a redirect). After users download the malware and enter their login and password on the fake page, fraudsters get a chance to remotely access the user's credentials or bank accounts. What we actually see here is a type of phishing conducted via technical remote access. Mobile and web technical remote access has also increased drastically. However, compared to October 2023, we may observe a slight drop in growth rates within markets equipped with up-to-date technological solutions.
- Active remote access based on social engineering technologies - based on social engineering, remote access supposes fraudsters remotely contact an individual. The idea is to persuade a user to install a particular app and then use it for fraudulent purposes. For instance, hackers may ask users to do certain actions that result in benefits or profits for online fraudsters. Here is an example: a fraudster contacts the victim by phone, messengers, or social network. A hacker tries to persuade a user to download a software or program and then gain remote access to the user's device. This is how scammers gain access to banking accounts and the opportunity of unauthorized money withdrawal.
- Passive remote access based on social engineering technologies – it happens when online fraudsters directly persuade a user to enter certain data for illegal purposes. Here is an example: fraudsters present themselves as bank employees. They contact the victim directly by phone, messengers, or social networks to affect the person through psychological manipulation. The idea is to persuade him to independently transfer money to the fraudsters' accounts.
Social engineering growth statistics
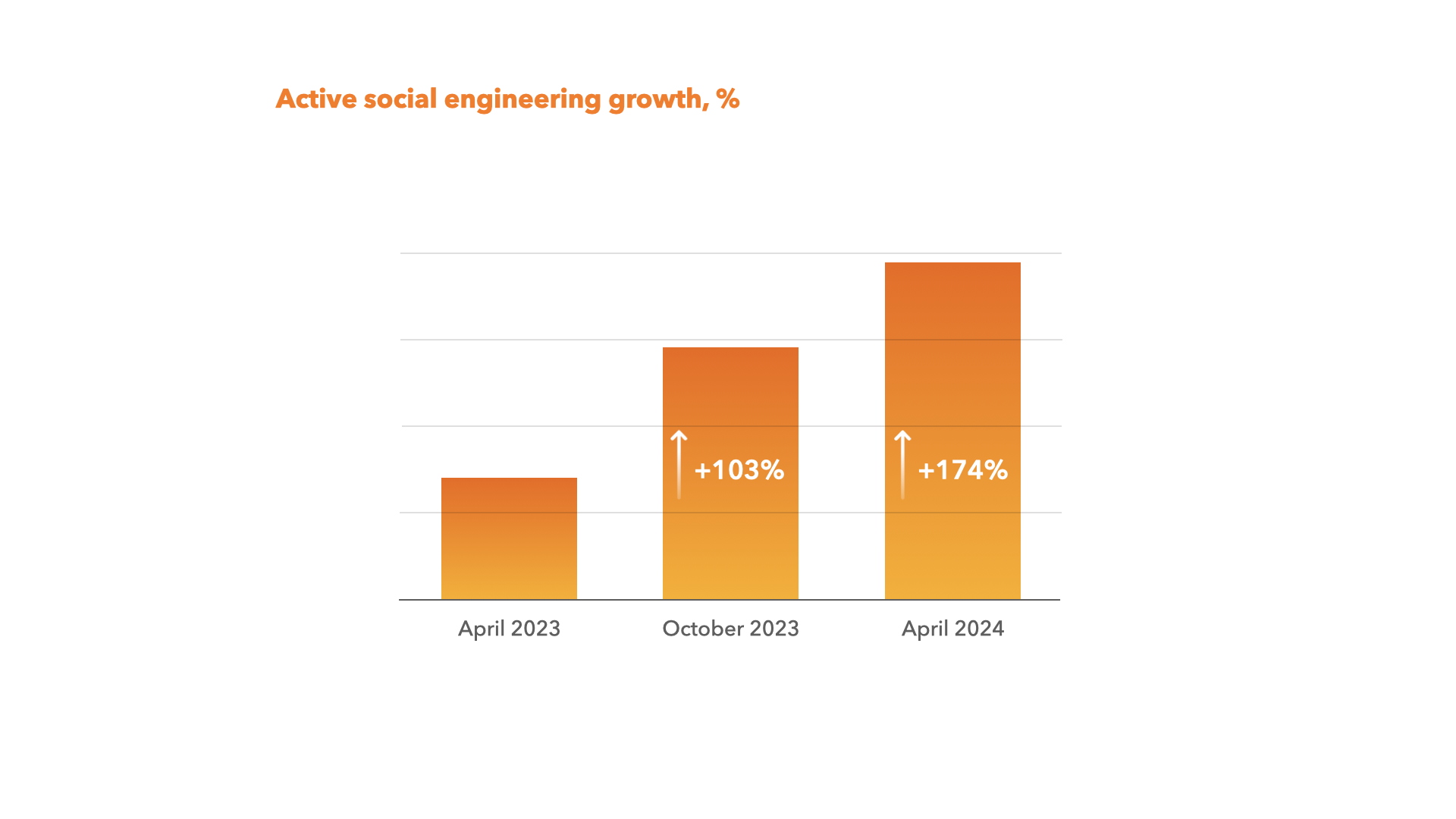
As you can see from the chart, active social engineering is growing at a staggering rate. Compared to April last year, we can see a 174% increase.
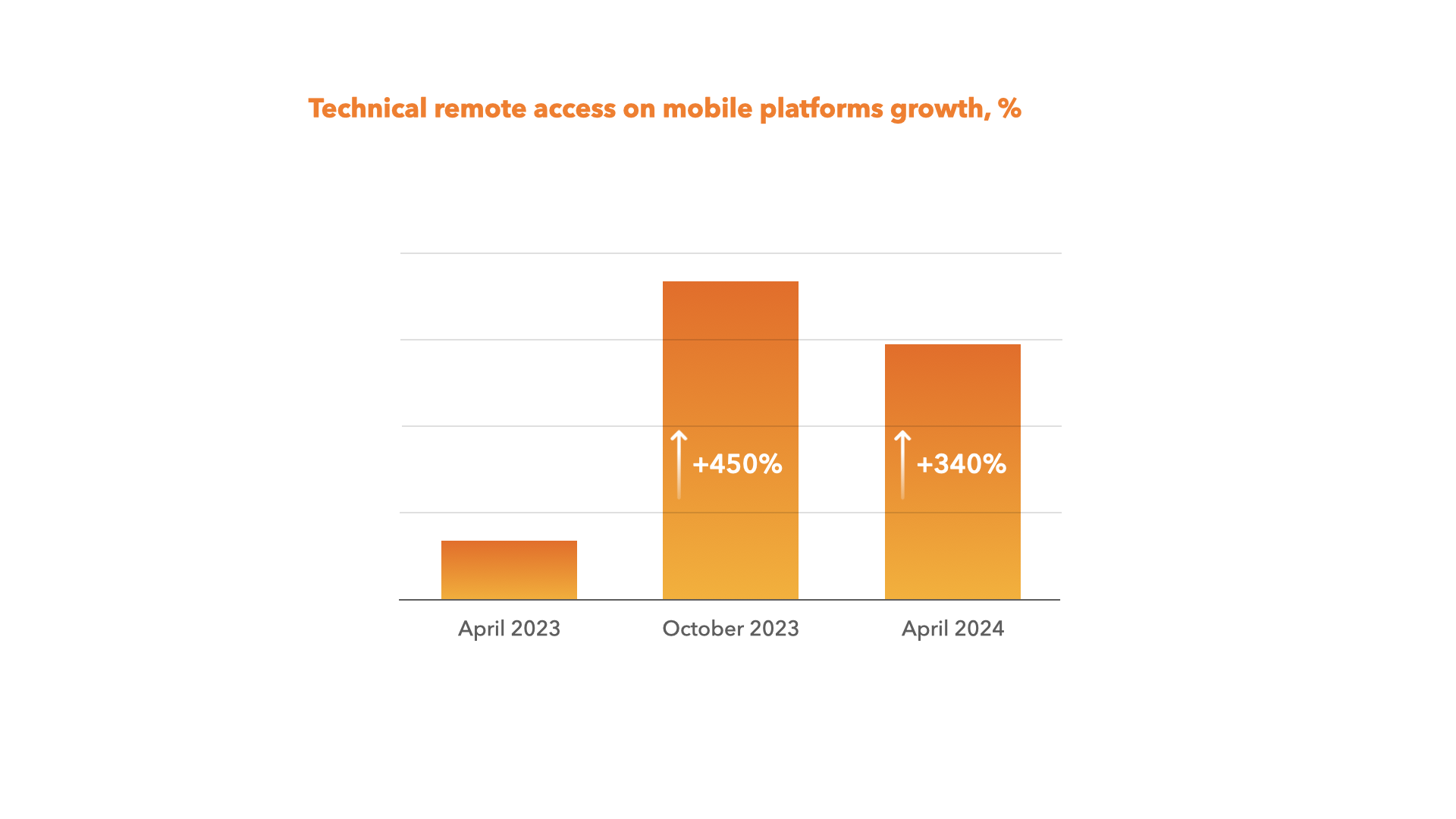
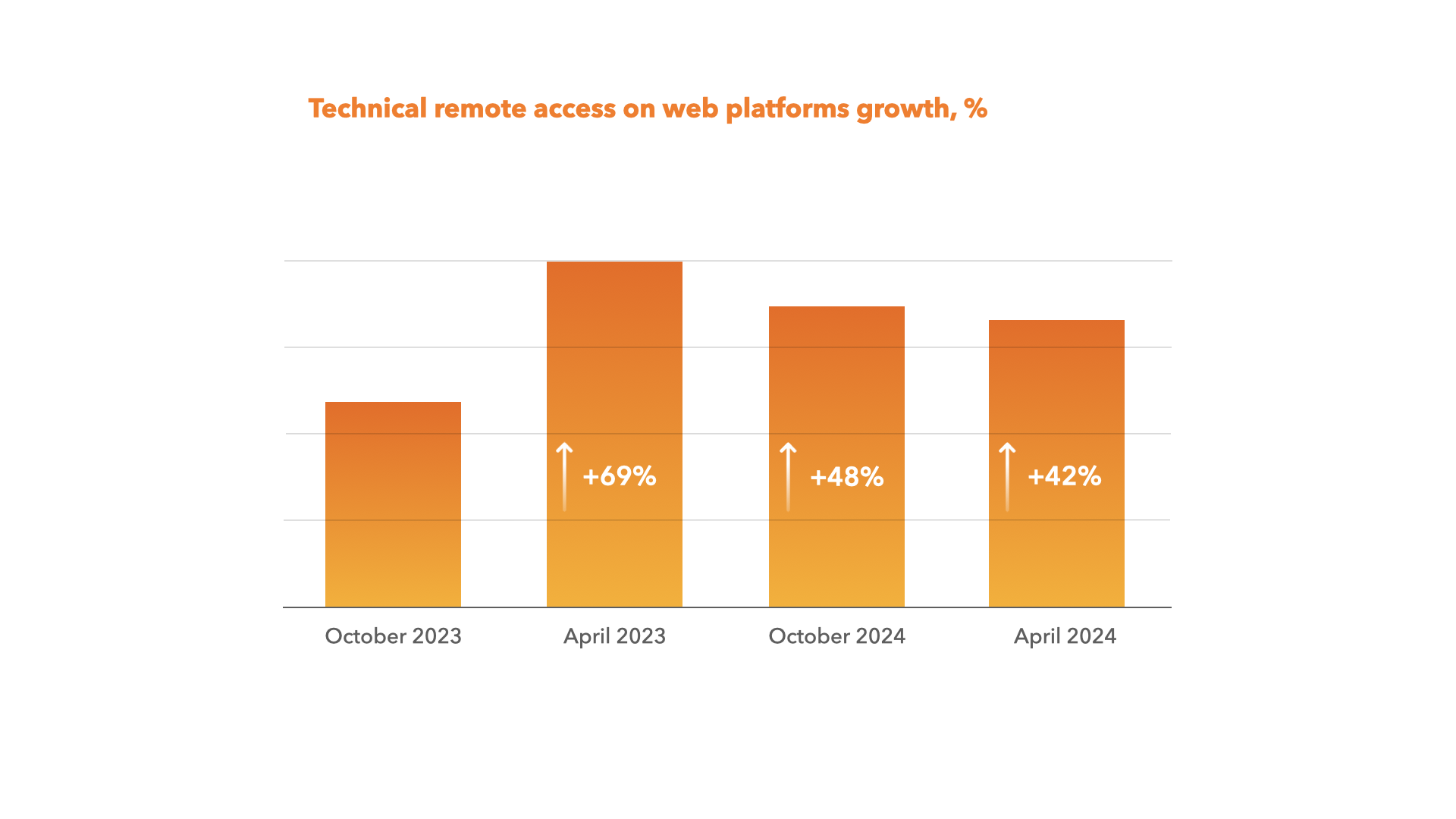
Social engineering is quite a broad term. It refers to a type of fraud where hackers use psychological manipulation to steal money, obtain users’ sensitive and personal data (e.g. passport details, online banking account login and password, etc.), or directly influence a user in any other scam way. Social media and phone calls are the main channels for performing fraudulent activities.
Trends to prevent and stop social engineering and fraud based on remote access technologies
For the past 3 years, JuicyScore's team has been actively testing various approaches to combat social engineering and technical remote access. The results prove that we have enough resources to solve this problem:
- For mobile devices (native SDKs) we practically managed to solve the problems of technical remote access and active social engineering based on the technologies of concurrent events analysis, the spectrum of running processes on the device, the structure of online user behavior, and anomalies. Right now, we are working out ways to resolve the issue of passive remote access based on social engineering technologies, which might require extra time.
- For web platforms – 2 years ago, we started testing solutions for technical remote access and active social engineering. The results are significant. We found it possible to reduce technical remote access in several countries where we actively help our customers. Working with web platforms can be quite specific. The work is based on analyzing a very large volume of graphical rendering anomalies, online user behavior, and online connection anomalies. We hope to expand the range of solutions that will be available in the next two API versions for JuicyScore and JuicyID.
Join us to become part of the JuicyScore team - a team that features an innovative and comprehensive perspective on how to establish risk-free digital risk management.
